Linset is a tool for Evil twin attack
How
it works
Scan the networks.
Select network.
Capture handshake (can be used without handshake)
We choose one of several web interfaces tailored for me (thanks to
the collaboration of the users)
Mounts one FakeAP imitating the original
A DHCP server is created on FakeAP
It creates a DNS server to redirect all requests to the Host
The web server with the selected interface is launched
The mechanism is launched to check the validity of the passwords
that will be introduced
It deauthentificate all users of the network, hoping to connect to
FakeAP and enter the password.
The attack will stop after the correct password checking
First of all download Linset
from github with command:
git clone https://github.com/vk496/linset.git
and then change the permissions of the linset script with command:
chmod +x linset
and then execute it with command:
./linset
After execution it will ask to choose the interface so select wlan0 for wireless extension which will
put it into monitor mode.
Then it will ask to select the channel so enter 1 to select all the channels.
Now the monitor mode will listen to all the
available wifi connections , so wait till your target appears and then press ctrl^c.
Now it will list all the AP’s
with their SSID ,id no. and signal strength , so enter the id of your target and hit Enter as in my case i have selected rajlab by entering 1.
Now select Hostapd by entering 1
which will help in creating Fake AP.
Now hit Enter for using
default path to save the capture file or you can give the custom path to save
the capture file which will ask to
select the method for cracking the handshake
so select 1 for aircrack-ng.
Now select 1 to de-authenticate all
the clients connected to the target AP to capture the handshake.
Now when the handshake is captured you will
see it on right top corner of the new window and then enter 1 on the menu window as we have captured the
handshake.
Now select 1 for web interface which will be presented
to the victim when he will connect to our fake AP.
Now it will ask for language selection of
the web interface so enter 1 for English.
Now 4 terminal windows will be opened of which one will create the Fake AP , one will be regularly de-authenticating
all the clients and one will show all
the info of the AP.
Now as you can see there are 2 rajlab AP are present of which one is
fake and open and the other is the original but the clients will not be able to
connect to the original one due to our deauth
attack so they will be forced to connect to our fake AP.
After connecting to the Fake AP it will redirect the victim browser
to below given web-page which will require the victim to enter the original AP password as the attack will only
stop when the victim will enter correct password.
After submitting the correct password , the attack will be stopped
and a message will be generated that your connection will be restored .
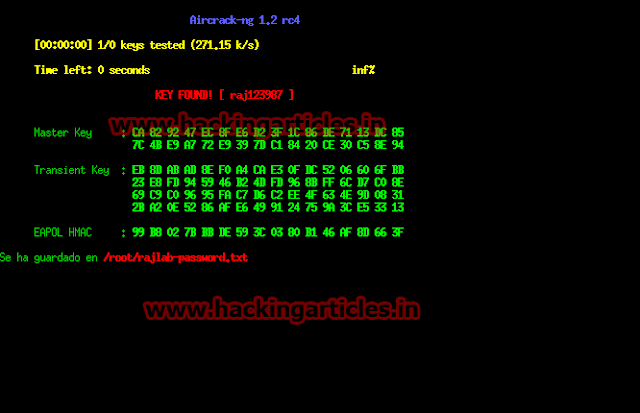
As you can see in my case victim entered the correct password and we
found the correct key as:
KEY FOUND! [ raj123987 ]























0 comments:
Post a Comment